Programming and Networking
Assignment #1: This first assignment was a collection of case studies that we responded to based on what we learned within the first few weeks: networking basics and the OSI model. This includes information about local area networks (LANs), the physical layer of OSI models (hubs, routers, switches, etc.), Wide Area Networks (WANs), and the basic cybersecurity principles (the CIA triad: confidentiality, integrity, and accessibility)
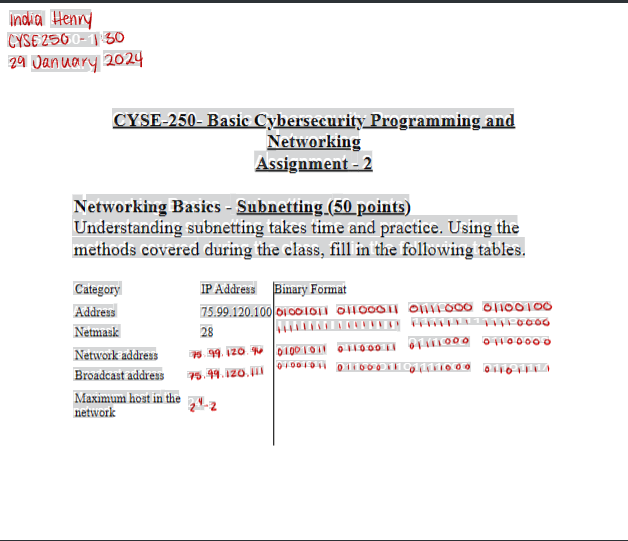
CYSE250-Assignment-1Assignment 2 – IP Adress and Subnetting: This assignment was to practice subnetting, which involves turning IP addresses into binary and manually running it through a netmask to get a network address and broadcast address.
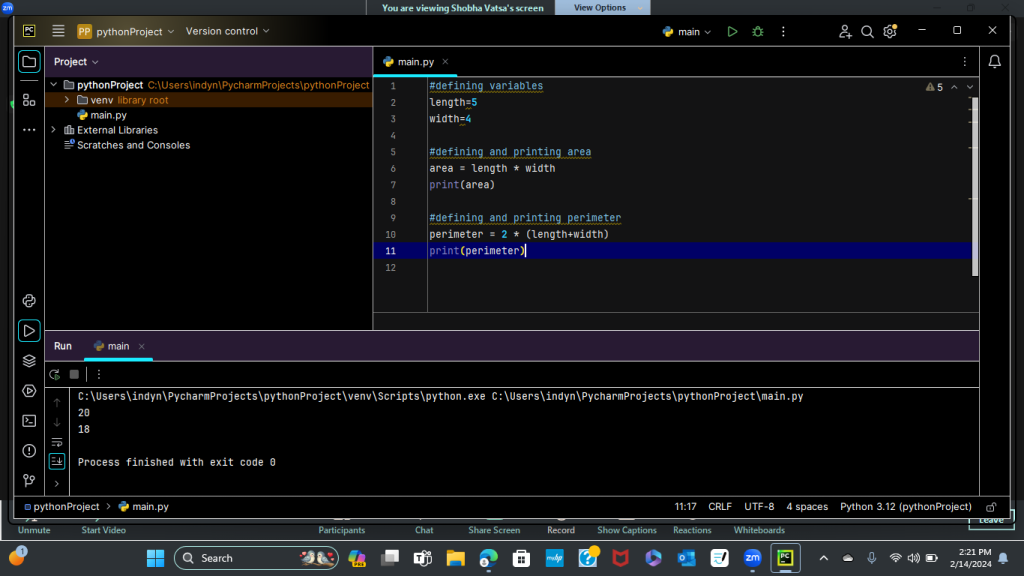
Introduction to Python Assignment 1: This is one of the first introduction to python examples we created in class. This assignment is amongst many others, which involved defining variables and equations then printing answers based on the information given. This example also shows proper documentation that would allow someone who has limited knowledge about programming to be able to follow along with the code.
Assignment 4 – Strings and Lists: This assignment walked us through the basic experience while programming in python. This assignment quizzed us on the different data types in python along with knowing the difference between them as well as how to use them. This assignment also asked us to write a program in python that took variables, required a basic equation, and needed the correct output to represent the equation.
assignment-week-7-Cybersecurity-Programming-CYSE250-1CYSE205-Assignment-W7
CYSE205-Assignment-W7-1
Assignment 5 – Data Types and Lists: This assignment focused on data types and being able to identify them. It also demonstrated how logic in python works when redefining variables. For the exercise in python, we wrote a program that takes user input of four numbers, averages them together, and prints the final product. The other python exercise required us to append, or add information to, an already established list.
assignment-week-8-Cybersecurity-Programming-CopyCYSE250-Assignment-W8-1
Assignment 6 – Tuple, Functions, and Modules in Python: This assignment was about functions, their importance, defining key commands, implementing functions into programs. Functions are important to keep programs readable; it allows the programmer to define an action one time, so it can be called multiple times in the program without the entire code needing to be rewritten.
CYSE250-Functions-Assignment-1Assignment 7 – Using If-Condition and Loops in Python: This assignment is based on the importance of conditionals and loops in python. Conditionals and loops work together in for and while loops so if the conditional is true, the program runs, but if the conditional is false the program exits out of the loop.
CYSE250-W10-Assignment-1Assignment 8 – While Loops in Python: This assignment focused on while loops and further defining what range commands mean in python. This assignment also introduces modules/libraries in python where we import libraries to be able to use different commands. For example, the pyfiglet module is imported to change the font of a given text and the math module is imported to give a wider range of math operations. There is also a program that take user input that is later used in the code.
CYSE250_-Assignment-8Assignment 9 – Socket Programming: This assignment asks about socket programming and communication servers. I’m asked to define some basic commands that come with importing the socket library as well as creating a socket program where a client and a server communicate with each other.
CYSE250-Assignment-9Distributed Denial of Service Research Paper: For the final research paper, my topic that relates to cybersecurity networking is the presence of denial of service and distributed denial of service (DDoS) attacks and how to mitigate them. This research paper uses a variety of scholarly journals that helps define what DDoS are and how to mitigate them.
CYSE250-Research-Assignment