CYSE 201S
Week 1 – Journal Entry | CYBERSECURITY & SOCIAL SCIENCE
The NICE Workforce Framework is a framework that is developed by the NIST (National Institute of Standards and Technology) and is used to define cybersecurity roles and responsibilities. The most interesting category to me is the Investigate category. The least interesting to me would be the Operate and Maintain component as it involves a day to day low-level work.
The Investigate section is defined by examining cybersecurity events, digital evidence, and instances of cybercrime. This is a role that involves interesting aspects of the criminal underworld and provides a deeper look into that world. As it is so shrouded in mystery, the cybercriminal world has an allure to it. Catching and holding criminals responsible is also a great moral motivator.
The role of Operating and Maintaining security frameworks is one that involves low-level “on-the-ground” work which can involve menial tasks. It is much more entertaining and fulfilling to lead and oversee an investigation into a criminal world.
Week 2 – Journal Entry | CYBERSECURITY & SOCIAL SCIENCE
Science has a strong relation to cybersecurity and the approach of analysis, and identification of threats.
Using empirical data is a cornerstone of proper cybersecurity operations as it allows the accurate identification and assessment of risk as well as developing the solutions needed to handle the threats.
The interdisciplinary nature of cybersecurity is one that closely relates to science as it integrates computer science and engineering to address technical and human threats.
A core component of a sound cybersecurity framework is the continuous adaptation and testing of protocols. Iteration and testing is a classical scientific practice and it is thoroughly used in cybersecurity.
Week 3 Journal Entry | CYBERSECURITY & SOCIAL SCIENCE
Researchers can use PrivacyRights.org to gather a lot of information about data breaches. Things like common denominators in vulnerabilities or attack vectors. Studying and understanding the prominent channels for attack allows researchers and professionals to better mitigate these issues. The database hosts an extensive amount of information related to breach notifications and reports. These are incredible resources for admins to use in order to better secure systems.
Overall, the publicly available information at PrivacyRights.org provides a rich foundation for a better understanding of the current cybersecurity landscape and data breach dynamics.
Week 4 – Journal Entry | CYBERSECURITY & SOCIAL SCIENCE
Maslow’s Hierarchy of Needs is a breakdown of humans’ most necessary needs for survival and a fulfilling life. As the internet has become prominent, it allows humans to achieve these needs from online sources. Here is a breakdown of each of them for myself.
- Psychological Needs – Technology plays a role in meeting the basic survival needs for myself. While technology isn’t itself food, water, or shelter, it helps me access these essentials.
- Safety Needs – Technology significantly contributes to my sense of safety and security. A password manager and two-factor authentication safeguard my personal data.
- Love and Belonging – Technology has become a crucial aspect of maintaining relationships. In my day to day life I stay in touch with loved ones through technology.
- Esteem Needs – Digital technology helps me contribute to my self-esteem through recognition of personal growth. It is valuable to look back and see how one has grown over the years and have it elevate our self esteem.
- Self-actualization – Technology plays a crucial role in my pursuit of personal growth and self-fulfilment. Building my online business is a perfect example of this.
Career paper
Decision-making, Rational Choice, and Policy Development
Social science underpins how analysts frame policies and relay risks to leaders. Using
frameworks such as Rational Choice Theory, analysts can forecast motivations for attack. A
state-sponsored perpetrator, for instance, could be motivated by geopolitical ends, while a
ransomware group could be influenced by short-term monetary incentive. Analysts can suggest
specific defensive measures based upon these motivations.
Additionally, behavioral economic concepts which study how individuals make decisions under
stress or with limited financial data guide analysts to devise employee training. It is designed to
remediate commonplace security breaches. Rather than applying policies based on reason
alone. Analysts therefore employ social science to provide situational and dynamic measures.
Social Implications and Marginalized Groups
Much of this intersection with social science lies with its application to marginalized
communities. Cybersecurity analysts recognize that marginalized communities are most likely to
be at risk of exploitation. For example, those who have low incomes do not necessarily have
devices that are secure, or may be scammed because of lacking digital literacy. Activists and
journalists, for example, can be singled out and targeted by actors who pose a threat in
authoritarian regimes.
Conclussion
Being a cybersecurity analyst is far removed from lines of code and servers, as it is as much a
job about individuals, trust, and behavior. Using the powers of social science, with its studies of
individuals, communities, and what motivates and affects them, analysts can learn more not just
about the attackers who threaten them, but also about the communities they protect. When it
comes to developing an equitable training program, tackling disparities of digital access, and
understanding what will, and won’t, make a difference with users, cybersecurity analysts draw
heavily on social science. As digital and social worlds become ever more entwined, experts like
these are critical to creating a safe and fair future.
Article Review #1: Factors Influencing Intellectual Security among University Students
Article Review #1: Factors Influencing Intellectual Security among University Students
Cristian Argint
CYSE 201S: Cybersecurity & Social Science
Professor Bora Aslan
Date 2/12/25
Article Review #1: Factors Influencing Intellectual Security among University
Intellectual security is the ability to critically evaluate information and resist ideological manipulation, making it essential to cybersecurity and social stability. The key component is to not fall for any misinformation or extremist ideologies. This content is often pushed by cybercriminals and at times through cybercrime to facilitate narratives of a certain group. The study titled “Factors Influencing the Formation of Intellectual Security among University Students: A Field Study” by Rommel et al. (2024) aims to identify the key factors that shape intellectual security among university students in Algeria and Jordan. Understanding these factors is important, as universities are breeding grounds for independent thought.
Research Questions and Hypotheses
The study examined intellectual security factors, gender differences, and educational level differences among students.
Research Methods and Types of Data Collected
The study used a cross-sectional research design, meaning that data was collected at a single time and not over a period.
The study surveyed 757 Algerian and Jordanian university students using purposive sampling, yielding 652 valid responses (86.12% response rate).
The variables measured were the following: Digital Media Influence, University Environment, Family’s Role, and Social Media’s Impact. All of these variables were measured within the context of how they impact intellectual security and the level of impact they had.
The data collected and analyzed was descriptive statistics, T-tests, and One-way ANOVA. Descriptive statistics refers to commonly used means and standard deviations. T-tests were used in the interpretation to account for gender differences. The ANOVA was used to tell apart the levels of education and if there was a relevant difference between the data between them.
Key Findings and Cybersecurity Implications
Digital media was the most influential factor, increasing phishing susceptibility and cognitive biases. University’s role in intellectual security was one that was key as well. The training of critical thinking skills is done but growing cyber threats were not referenced often in curriculums. Families influence on cyber-awareness either enhance or degrade a student’s ability to evaluate real-world cyber threats and manipulation. The psychodynamic theory of early childhood experiences shaping a child’s resilience to these events is relevant in this aspect. If a family was focused on exposing their children to such mediums at an early age, the students often turned out resilient to cyber threats and corruption of their intellectual ideas. There were no significant differences between genders or academic levels.
Marginalized groups face higher cyber fraud risks due to limited cybersecurity education, making them prime targets for cybercriminals. Potential solutions to the problem include government funded cybersecurity training and education for these marginalized groups to increase digital literacy in low income communities.
Conclusion
The study highlights important factors when it comes to intellectual security and the influence that cybersecurity has on it. Digital media is a double edged sword that is useful for education but a risk factor for cyber manipulation. Universities have often lacked behind when it comes to cybersecurity training in regard to real-time occurrences. Future studies should assess digital media’s long-term effects on cybersecurity awareness.
References
Al-Halalat, K. I., Beichi, A., Al-Barakat, A. A., AlAli, R. M., Al-Saud, K. M., & Aboud, Y. Z. (2024). Factors influencing the formation of intellectual security among university students: A field study. International Journal of Cyber Criminology, 18(1), 108–129. https://cybercrimejournal.com/menuscript/index.php/cybercrimejournal/article/view/344/101
Article Review #1: Factors Influencing Intellectual Security among University
Students
Cristian Argint
CYSE 201S: Cybersecurity & Social Science
Professor Bora Aslan
Date 2/12/252
Article Review #1: Factors Influencing Intellectual Security among University
Intellectual security is the ability to critically evaluate information and resist ideological
manipulation, making it essential to cybersecurity and social stability. The key component is to
not fall for any misinformation or extremist ideologies. This content is often pushed by
cybercriminals and at times through cybercrime to facilitate narratives of a certain group. The
study titled “Factors Influencing the Formation of Intellectual Security among University
Students: A Field Study” by Rommel et al. (2024) aims to identify the key factors that shape
intellectual security among university students in Algeria and Jordan. Understanding these
factors is important, as universities are breeding grounds for independent thought.
Research Questions and Hypotheses
The study examined intellectual security factors, gender differences, and educational
level differences among students.
Research Methods and Types of Data Collected
The study used a cross-sectional research design, meaning that data was collected at a
single time and not over a period.
The study surveyed 757 Algerian and Jordanian university students using purposive
sampling, yielding 652 valid responses (86.12% response rate).
The variables measured were the following: Digital Media Influence, University
Environment, Family’s Role, and Social Media’s Impact. All of these variables were measured
within the context of how they impact intellectual security and the level of impact they had.
The data collected and analyzed was descriptive statistics, T-tests, and One-way
ANOVA. Descriptive statistics refers to commonly used means and standard deviations. T-tests
were used in the interpretation to account for gender differences. The ANOVA was used to tell3
apart the levels of education and if there was a relevant difference between the data between
them.
Key Findings and Cybersecurity Implications
Digital media was the most influential factor, increasing phishing susceptibility and
cognitive biases. University’s role in intellectual security was one that was key as well. The
training of critical thinking skills is done but growing cyber threats were not referenced often in
curriculums. Families influence on cyber-awareness either enhance or degrade a student’s ability
to evaluate real-world cyber threats and manipulation. The psychodynamic theory of early
childhood experiences shaping a child’s resilience to these events is relevant in this aspect. If a
family was focused on exposing their children to such mediums at an early age, the students
often turned out resilient to cyber threats and corruption of their intellectual ideas. There were no
significant differences between genders or academic levels.
Marginalized groups face higher cyber fraud risks due to limited cybersecurity education,
making them prime targets for cybercriminals. Potential solutions to the problem include
government funded cybersecurity training and education for these marginalized groups to
increase digital literacy in low income communities.
Conclusion
The study highlights important factors when it comes to intellectual security and the
influence that cybersecurity has on it. Digital media is a double edged sword that is useful for
education but a risk factor for cyber manipulation. Universities have often lacked behind when it
comes to cybersecurity training in regard to real-time occurrences. Future studies should assess
digital media’s long-term effects on cybersecurity awareness.4
References
Al-Halalat, K. I., Beichi, A., Al-Barakat, A. A., AlAli, R. M., Al-Saud, K. M., & Aboud, Y. Z.
(2024). Factors influencing the formation of intellectual security among university
students: A field study. International Journal of Cyber Criminology, 18(1), 108–129.
https://cybercrimejournal.com/menuscript/index.php/cybercrimejournal/article/view/344/
101
Week 5 Journal Entry
#1 Recognition – Cybercriminals seek status within their communities, this is a great way to do that.
#2 Political – Often ideologically driven and comes from something greater than the person.
#3 Money – Financial criminals often hack for monetary gain. The exploitation of financial systems is purely for profit.
#4 Revenge – This is often driven by ideological or emotional motives and again can be bigger than oneself.
#5 Multiple Reasons – Some cybercriminals have a mix or reasons and take advantage of a perfect opportunity.
#6 Entertainment – Having power over an organization is a powerful motivator for hackers to exude their power and feel powerful.
#7 Boredom – Cybercriminals like all criminals are often illogical and reckless and thus due to boredom they initiate crimes.
Week 6 Journal Entry
Below is a screenshot from a fake Meta Business Center site.
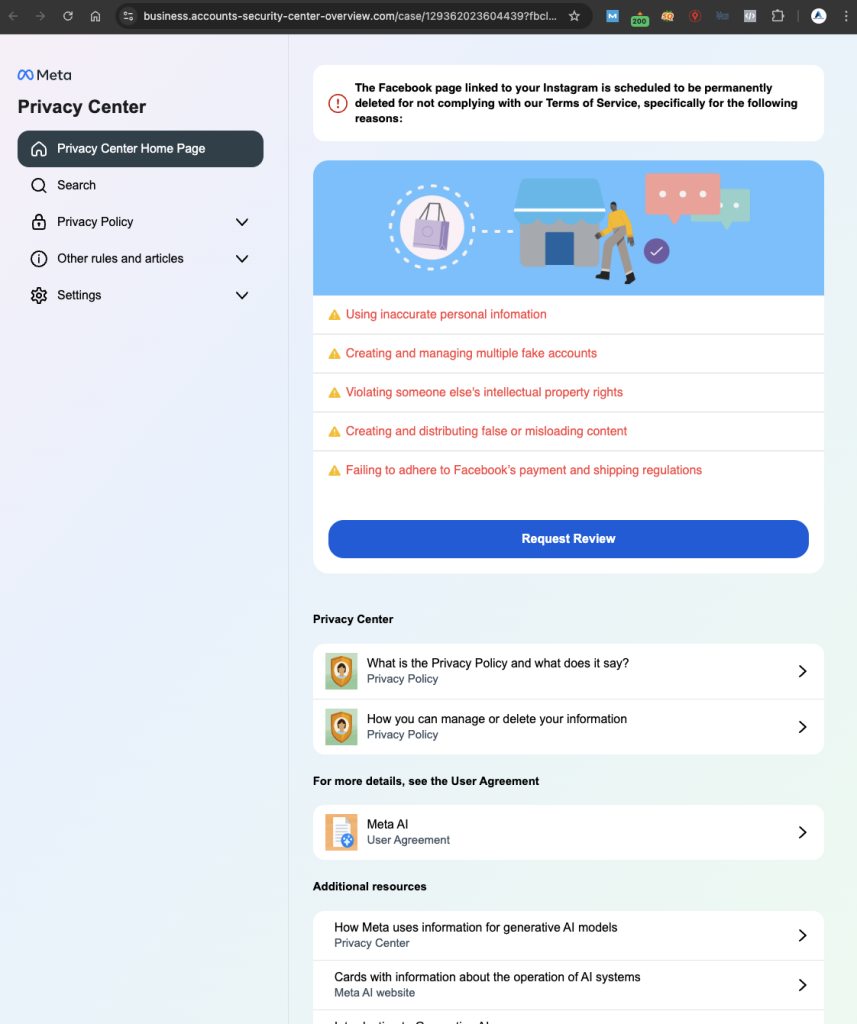
The site looks legitimate and as if it is from Meta but it is not. Looking at the URL above, there is no base facebook.com URL or subdomain. Upon clicking the Request Review button, there is a contact form that appears requesting personal information. It is important to check the URL of the site, as well as any links and minor details within it. In this case, the Terms of use anchor text is not an actual link. It does nothing.
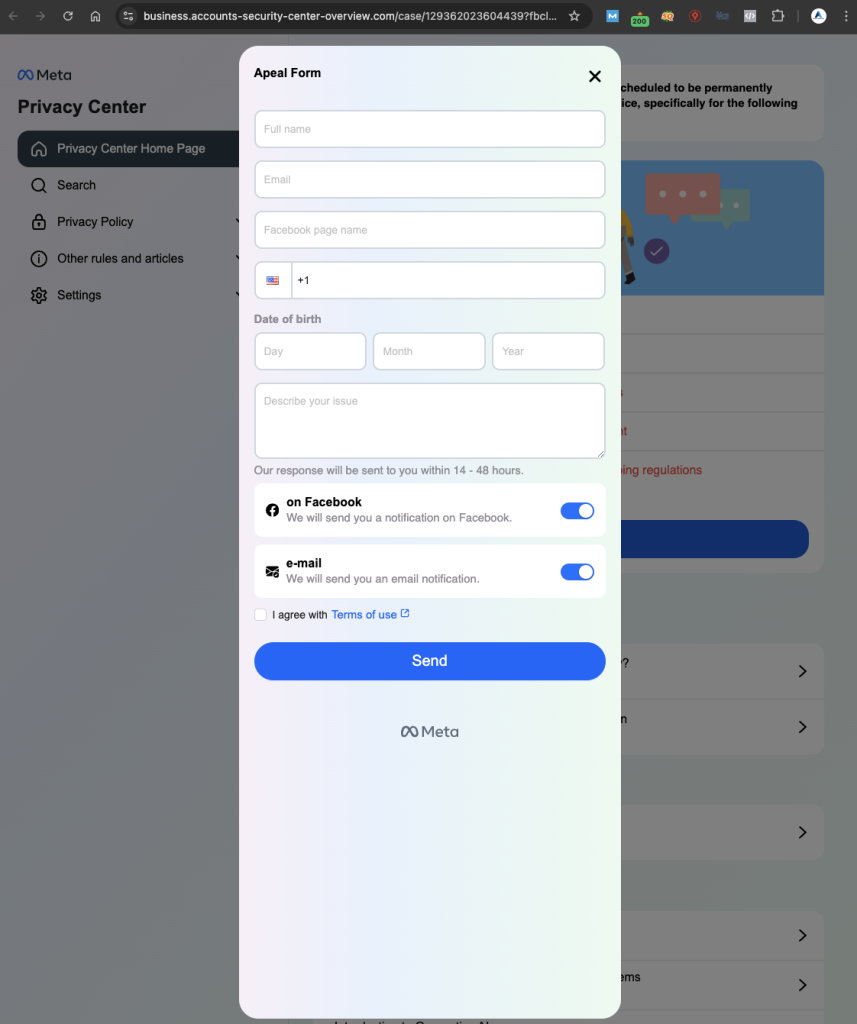
Week 7 Journal Entry

Week 8 Journal Entry
The video titled Hacker Rates “12 Hacking Scenes In Movies And TV | How Real Is It?” is a great insight into the stark difference between how Hackers are portrayed in media compared to how hackers truly operate. Movies and media often imagine hacking software to look dynamic with a green and black terminal, maybe a hacking room with advanced computers and devices. The reality is that hacking is a basic process of someone using a computer and not necessarily any advanced technology. Hacking can be done by anyone with a computer from anywhere in the world. Although these movies are entertaining to watch, it is important to understand what real hacking looks like and not be mislead by flashy movies.
Week 10 Journal Entry
Social Media Disorder Scale (SMD Scale)
Please answer the question by thinking of your experience with
using social media (e.g., WhatsApp, SnapChat, Instagram,
Twitter, Facebook, Google+, Pintrist, forums, weblogs) in past
year. Answer the questions as honestly as possible. According
to DSM, at least five (out of the nine) criteria must be met for a
formal diagnosis of “disordered social media user”.
During the past year have you…
- Regularly found that you can’t think of anything else but
the moment you will be able to use social media again?
Yes/No (Preoccupation). - Regularly felt dissatisfied because you want to spend more
time on social media? Yes/No (Tolerance). - Often felt bad when you could not use social media?
Yes/No (Withdrawal). - Tried to spend less time on social media, but failed?
Yes/No (Persistence). - Regularly neglected other activities (i.e. hobbies, sports,
homework) because you wanted to use social media?
Yes/No (Displacement). - Regularly had arguments with others because of your
social media use? Yes/No (Problems). - Regularly led to your parents or friends about the amount
of time you spend on social media? Yes/No (Deception). - Often used social media to escape from negative feelings?
Yes/No (Escape). - Had serious conflict with parents, brother, sister (friends,
relationships etc.) because of your social media use?
Yes/No (Conflict).
9-item scale measures adolescents degress of addiction to
social media. Based on scale from Internet Gaming Disorder
found in the DSM-V, for preoccupation, tolerance, escape,
persistence, withdrawal, conflict, problems, deception, and
displacement. (n= 724), reliability good.
Van den Erjnden, RJ.J.M., Lemmons, J.S., & Valkensburg P.M.
(2016). The Social Media Disorder Scale. Computers in Human
Behavior, 61, 478-487.
I scored ok for this and do not have any issues with social media. I think it is crucial for parents to evaluate their children’s social media use and act accordingly.
Week 11 Journal Entry
After reading “Social Cybersecurity: An Emerging National Security Requirement,” I realized how cybersecurity is no longer just about protecting systems—it’s also about protecting people and society from manipulation. The article explains how state and nonstate actors use technology to influence beliefs, spread misinformation, and weaken national unity. This form of warfare, called social cybersecurity or “cognitive hacking,” targets human behavior rather than just machines.
One part that stood out to me was how these tactics are used to break trust in institutions and values before any physical conflict begins. It’s a modern version of psychological warfare, using social media and data-driven strategies to divide populations. What makes it more dangerous is how fast and invisible it can be.
This article made me think about how the future of cybersecurity must involve not just IT experts but also social scientists, psychologists, and policy makers. Defending against digital threats now requires understanding human behavior as much as understanding firewalls.
The video highlights how the role of a cybersecurity analyst extends beyond just technical skills—it also involves understanding human behavior. Analysts are tasked with identifying and responding to threats that often originate from social behaviors, like phishing attacks or poor password practices. A major theme is how cybersecurity involves educating and working with people across an organization to build a security-conscious culture. Communication, teamwork, and awareness are emphasized just as much as coding or threat detection. These social elements show that cybersecurity analysts act as both technical defenders and human behavior observers, helping shape how users interact safely with technology.
Week 12 Journal Entry
The sample data breach letter from GlassWasherParts.com reveals how a security incident can have broad economic and social implications. Two economic theories that relate to this scenario are Cost-Benefit Analysis and Externalities. First, businesses often weigh the cost of stronger security controls versus the likelihood of a breach—this breach may show that the platform provider undervalued the cost of a potential attack. Second, externalities are present because customers are suffering the consequences (e.g., identity theft risk) of the company’s security failure—costs that weren’t factored into the provider’s initial risk management.
From a social science perspective, Rational Choice Theory and Social Trust Theory apply. The hackers made a calculated decision to exploit a weak system in exchange for a potential financial reward, which aligns with Rational Choice Theory. Meanwhile, the incident damages Social Trust—customers may no longer trust the company to protect their information, affecting future purchasing behavior and public perception.
Overall, this case shows how cybersecurity decisions impact not just technology, but also people and the economy.
Week 13 Journal Entry
The article presents a strong case for the use of bug bounty programs as a cost-effective cybersecurity strategy. From the literature review, we learn that these programs address two major challenges: the global shortage of cybersecurity talent and the need for diverse perspectives to discover hidden vulnerabilities. Unlike traditional hiring, bug bounties allow companies—especially small and mid-sized ones—to crowdsource talent and receive security feedback from ethical hackers around the world. This gig-economy model is not only flexible but also democratizes access to cybersecurity expertise.
In the discussion of findings, the authors analyze HackerOne data to show that hackers are relatively price inelastic, meaning they are motivated by more than just money—such as reputation building, experience, and altruism. This is encouraging for companies with smaller budgets. Another key takeaway is that a company’s revenue or brand doesn’t significantly affect how many bug reports it receives. In fact, even lesser-known companies can benefit. One downside noted is that bug reports decrease over time unless a program expands its scope. Also, companies in finance and healthcare may receive fewer reports, possibly because those vulnerabilities can be sold on black markets instead. Overall, bug bounty programs appear to be a valuable and sustainable component of cybersecurity policy.
Week 14 Journal Entry
The five most serious online violations are cyberbullying, identity fraud, illegal torrenting, sharing private info without consent, and collecting data on children. Cyberbullying and identity fraud can cause real emotional and financial harm. Torrenting breaks copyright laws and spreads malware. Sharing personal info without consent violates privacy, and collecting kids’ data is illegal under COPPA. These are serious because they directly harm people and often target vulnerable users.
Week 15 Journal Entry
In his TEDx talk, Davin Teo explains how digital forensics is not just about computers and technology, but also about understanding people. His career path shows that solving cybercrimes requires knowledge of psychology, sociology, and human behavior. Digital forensic investigators must figure out not only how a crime was committed but also why someone did it. Teo highlights that technology changes fast, but human nature stays the same, so investigators need strong social science skills to analyze motives, reconstruct actions, and interpret digital evidence accurately. His journey shows how important it is to blend technical expertise with an understanding of social factors when working in cybersecurity.
