The five most serious violations that people commit online I think are Faking your identity, Bullying and Trolling, Sharing Passwords, Addresses or photos of others, Illegal Internet searches and collecting information about children. The reason faking your identity is bad because people do that to steal people’s money or commit crimes which hold the persons who identity they stole to be held accountable it can easily destroy someone’s life and it is hard to fix. Bullying and Trolling is something that is pretty common online now and it can be very dangerous because people have been known to commit suicide because of it. Collecting information about children is a big one because no one needs to have personal information on children except the parents and children’s information can be used to commit a number of crimes. Illegal searches on the internet is another big one because there is some information that should not be on the internet but is and people should not be trying to find it this ties in with information about children, illegal searches are just bad all the way around. Sharing passwords, addresses and photos of others is bad because that’s someone else’s information and should not be shared and ties into everything else listed here. The article talks about using VPNs and everything to protect yourself from some of this stuff but it’s a two-way street here yes, they can protect innocent people accidently making an incorrect search, but it also protects criminals doing it intentionally.
Category: Journal
Journal Entries for CYSE 201S
Deontology
In the comic “What’s so Funny About Truth Justice and The American way?” Superman is faced with the Elite. The Elite is a group of enhanced beings that think they are heroes because they are ridding the world of criminals by killing them. Their thought on why they believe this is okay is reinforced by the people that cheer for them and think they are doing the right thing. But Superman knows this is wrong, at least for him in his mind.
Immanuel Kant’s view that someone could do something that is good but for the wrong reasons is still wrong. In the comic, a kid dressed as Superman says, “I can’t kill, but you can kill me! How can I stop you if I can’t kill?” which tells Superman that people are starting to think that killing criminals is the only way to stop them. Superman sees killing as wrong even if they are bad people that are killed to make the world better, and it is still wrong to kill. He never bends on his moral standing, even if it means he must die for his beliefs. Superman stands up to the Elite first by trying to show them they can fight criminals without killing them. This backfired a bit because the elite knew the criminals Superman caught would do it again and again. Superman’s response was that he would stop them again and again until they understood that its wrong. Superman held to Kant’s imperative by doing what was right not just for him but for others. If killing is wrong and a crime. Then killing is wrong and a crime even for those that kill people for the good of others.
This is a view the Elite did not share. They believed that killing the bad guys would make them the good guys. They also thought they could get Superman to agree with their line of thinking. They went around killing many people, saying it was for the sake of others, and called themselves heroes for it. Not knowing this made them no better than the bad guys they killed. Committing a crime to prevent a crime is still wrong. They became the very thing they were trying to get rid of. There is no justification for it. Superman wins the fight by getting Black to believe Superman killed his team and calls Superman a hypocrite. Superman only made it look like he did to beat them at their own game and to make his point even more vital. That he would not bend on his moral reasoning that killing is wrong and that there is always another way to fight criminals without becoming one yourself, Black said he would come after Superman as long as he still lives. Superman replies, “I wouldn’t have it any other way.” Because he knows that no matter what, he will stop him or die trying because it is the right thing to do, not just for him but for everybody.
Ethics of care
The Mother of Invention goes over how people treat each other based on their choices or understanding of each other. In Anwuli’s case, her friends and family judged her and shunned her for her relationship with a married man. Although what she did on the outside seems morally wrong to her friends and family. None of them even bothered to listen to her side of the story. How she should have been treated is far different than how everyone around her treated her.
The way Anwuli should have been treated by her neighbors, friends, and family should have been with respect and care. They should not have judged her and listened to her side of what happened. She was the one that was deceived and seduced by a married man, yet they took his word for what happened and blamed her. They should have helped her and listened to her, especially her family. They should never have abandoned her for what took place and been there to welcome her baby into the world.
Anwuli’s neighbors, friends, and family did not act in a caring way. Instead, they acted in a way that we see people do all too commonly today. They were judgmental and assumed the worse of her. They would not even let her explain her side of the story. By being judgmental, they sought justice for her ex-fiancé, the married man that did her wrong. So, they chose to shun her and block her on social media as punishment for the crime they assumed they thought she had committed. They did not try to fix or change their actions to improve the relationship so that they could flourish as a family, friend, or neighbor; instead, they just abandoned her.
Anwuli’s fiancé should have treated her with respect despite his deception; he should have taken responsibility for his actions. He should have shown her that he cared about her and his child’s well-being. Despite his moral failure to be faithful to his wife, he should have ensured the safety of Anwuli and his soon-to-be baby and protected her. He should have taken her to the hospital despite his wife’s say on the matter. He failed when he left her alone and gave people a reason to judge her for something she did not do but for what he did to her. If he had given her the respect and care she gave him, they could have both handled the situation better and improved the whole situation. His actions led to her being alone with no one to talk to or help her with his child.
The house Obi 3 showed more caring than anyone around Anwuli even though it did not have emotion. The house recognized the needs that needed to be fulfilled and tended to those needs for her, unlike everyone else around her, who ignored her, and her needs based on their judgment about her. They deemed her better off dead. Obi 3 exhibited caring behavior because it was designed to do just that protect the people inside the house. It did not judge her or her actions. Just like Anwuli’s body or any female body is designed to care for and protect a fetus before birth. It is not emotional; it is just how it was designed, just like how our bodies are designed to sustain life without judgment.
The video Obi 3 plays show that despite the past faults about the oil extraction, the peri grass was created to apologize for what they did to the land. It was also an attempt to make up for the damage they had created while extracting the oil. It shows that they care about the Nigerian people. They took responsibility for their actions from the past so they all could grow together.
Module 10 Entry
The article on social cybersecurity details the different types of social cybersecurity attacks and outlines what we need to do to defend against them. There are different types of social cybersecurity maneuvers to look out for, such as information and network maneuvers. The information maneuver is done by manipulation of information and the flow or relevance of information. Tools used in this maneuver are misdirection, hashtag latching, smoke screening, and thread jacking. The network maneuver is the manipulation of the actual network. Tools used in network manipulation are opinion leader co-opting, community building, community bridging, and false generalized other. These types of attacks are being used on societies to weaken them so an adversary can easily defeat them. They do this by getting society to crumble from within, creating distrust and chaos in their society. The article also explains how bots can help do this at a much larger and faster scale. In conclusion, it talks about how military leaders and the D.O.D. need to understand these types of attacks and look out for them within their authority while educating the public about them indirectly. It must be done ethically and quickly. We also need to develop policies to help defend against them and seek to remove any wedge of distrust between our military and society.
Module 9 Entry
My social media disorder score was 0. I think the items on the scale are relevant and can help people identify if they have a problem, but only if they are honest with themselves because people can lie to themselves, refuse to see the problem, and not change. I believe different patterns are seen worldwide because of location and access to technology or the internet. Some places cannot get internet, and some areas are in poverty, unable to access social media, or it makes it hard for people to become addicted to something they cannot access. Also, in areas where many people can access it, the numbers can vary depending on situations, how people were raised or what beliefs they may have. So, patterns around the world can be very different when it comes to social media.
Module 8 Entry
After watching the video, I think the media shows that hacking is cool and something only brilliant people can do. In reality, almost anyone can hack. Some media also shows how scary it can be if it were to happen in real life. Most of the things that were rated in the video were pretty realistic. Some things were just Holly Wood trying to make the scene look better. I think the media tries to show hacking as fun and that everyone should do it when, in reality, it’s dangerous and mostly illegal. The fact that some of these shows were realistic makes them more attractive. It also helps pull people into the Cyber Security field.
Module 7 Entry










My memes relate to human systems integration because everything captured in these memes is done with technology and system integration with humans. This technology lets people take pictures or do their jobs in any environment and allows people to interact no matter where they are.
Article Review 2
My review of the article “I Can be a Super Sleuth: Promising Practices of Engaging Adolescent Girls in Cybersecurity Education” points out why there are not many girls in the cybersecurity field. The study shows some of the reasons why girls are not engaged in the cybersecurity field. It is basically the same reason girls are not usually into video games. It is stereotypically viewed as nerdy and nonsocial. It also explains the need for women in cyber security and how diversity is essential so every avenue of cyber security can be implemented. Since there are so few females in the cyber security field, girls lack role models that help get them interested in computer science careers. Studies have shown that girls have lowered feelings of belonging in the computer science field; as a result, very few women seek a career in computer science. In class, we have discussed that women were less inclined to be in a computer science field due to certain factors, mainly that they have a disinterest in them for one reason or another and this article’s studies support that. They also found that in cyber security, there were misconceptions about who is entitled to participate. This acted as a barrier for women to get into the cybersecurity field. They also found out they had almost no data about what adolescent girls perceived of the cybersecurity Field. So, they had a study for just 38 adolescent girls to help research that answers two questions how girls perceive cybersecurity and what practices can engage girls in cybersecurity. They also found that girls blame their lack of ability and self-efficacy for not going into the field. These reasons are why girls would withdraw from the field. They also found out that girls enjoy puzzles and solving real-world problems. Because of this, girls can be interested in computer forensics. The study of the 38 girls was done in a summer program, and it went over cyber security basics and had teachers that took their time with each individual student to help them understand the material. As a result, the girls enjoyed working on the cyber security assignments and said they would not mind a career in the cyber security field. So, the study showed that having good teachers and the class is only for girls helped raise girls’ interest in the subject because they did not feel intimidated by boys. After all, there were none. The teachers were patient with them and made them feel comfortable with the material, and they didn’t have the feeling of being pushed down or overshadowed like they would in a co-ed setting. So, eliminating some stereotypes could help more girls choose to be in cyber security. The studies also mention that there needs to be more studies on girls with no prior interest in computer science. These studies could help fill the gender gaps in cyber security. I think this article hits on key points, and they need to find better ways not just to get girls interested in the field but have a way, so boys don’t give girls a feeling of being pushed down or overshadowed.
Module 6 Entry
Three ways to identify a fake website are first by checking the TLS/SSL certificate usually if there is a closed lock next to the URL the site is legit. The TLS/SSL certificate has 3 validations domain validation certificate which verifies ownership of the domain. Next is Organization Validation certificate which is authenticated by the certificate authority in official business registration. Third is Extended validation certificate which contains other validation processes to protect brand and users. Also, most browsers will give you a warning saying the site is not secure. This can be a way of finding out if a website is fake. Another way to spot a fake website would be it is incorrectly spelled or has no contact information or correct contact information for the business.
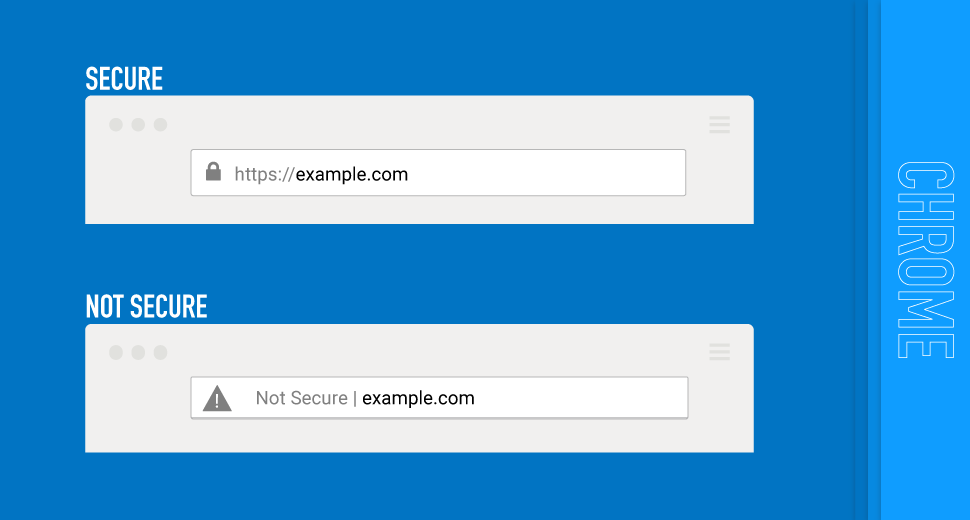
Module 5 Entry
I think the motive to make money makes the most sense as to why people commit cybercrimes. This is number one. Number two would be revenge people do a lot of crazy stuff to get back at someone that hurt them. Number three would be Political because they have a political goal and are willing to do anything to achieve it. Four and five are a tie for me because Entertainment goes with boredom. If you are bored, you seek to be entertained somehow. Number six would be multiple reasons a person commits a cybercrime. It may be several factors as to why they do it. Number seven makes the least sense to me that doing a crime for recognition is self-destructive yea you may get recognized for a short period, but you can be in prison for a very long time.
